Documentation
This is the I N P R O G R E S S administrator documentation. For a general overview of vulture or the installation documentation click respectively on Vulture or Installation in the right menu.
Vulture is an HTTP reverse proxy. It does many security checks (authentication, rewriting, filtering) before proxying request from Internet to your web applications. With authentication enabled, vulture will open flows only to authenticated users. It also allows to your users to use only one password to access many different applications by learning and forwarding their different accounts.
Vulture includes :
- Authentication (SSL, LDAP/AD, SQL, Radius)
- Authentication forwarding (SSO)
- HTTP headers modification on the fly
- Flow encryption
- Content filtering
- URL Rewriting
- Load balancing
Administration logging in
When Vulture is installed, go to https://localhost:9090. You may need to do a ssh forward or editing conf/httpd.conf in order to get apache listening on another IP if you don’t run your browser from the host running vulture. The default password for admin is admin

Modifying the administrator password
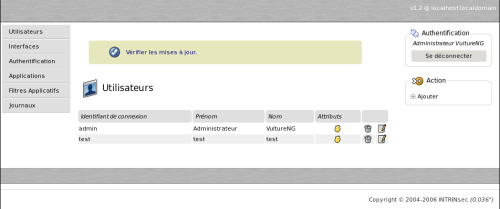
After logging in, the page below will come up. The icon
 means that the user is an
administrator. We will see thereafter why non administrator users can
be usefull. Click on
means that the user is an
administrator. We will see thereafter why non administrator users can
be usefull. Click on  to change the password
of “admin”.
to change the password
of “admin”.

Adding an interface
An interface is most likely an Apache process. By adding or editing an interface you will specify most of the apache options (ip and port, certificat, log format). Thereafter, we will bind applications on this interface and look at SSL and « SSO portal » features.

Back to the interface list you can see thoses icons :
 : interface is up and running
: interface is up and running
 : interface is down
: interface is down
 : click on it to stop an interface
: click on it to stop an interface
 : click on it to commit changes and start or restart the interface
: click on it to commit changes and start or restart the interface
Leave the interface stopped as we dont have an application configured on it yet.

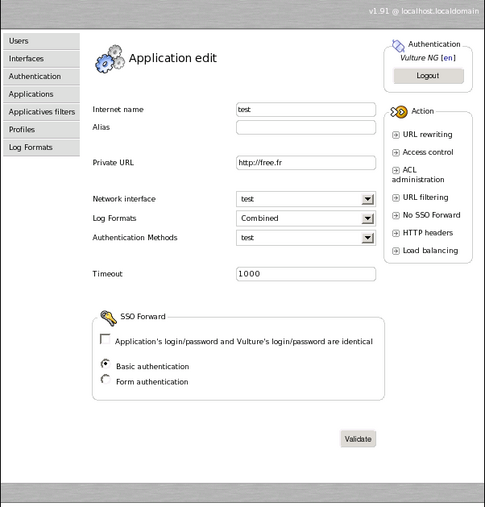
Adding an application
An application is mainly represented by its internet name. This is what users will type in the URL bar to join our application. Vulture will answer by providing content from the private URL. This is reverse proxying. We will see thereafter how vulture can require authentication before providing anything from the private URL. Add an application as shown below and start the interface.
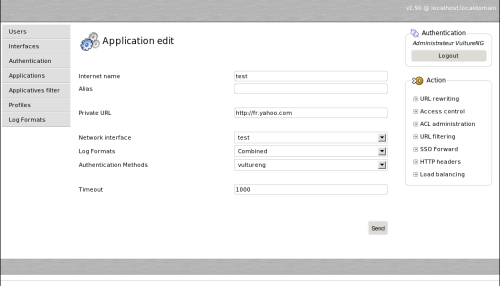
Go back to the interface menu and start the interface. You should be able to type http://test or whatever you set the application name to and see your application. If you don’t, go to the FAQ menu.

Authentication
Now that you have an application up and running let’s see how to restrict access to authorized users only. Vulture support LDAP, SQL, Radius and x509 client certificat authentication.
We first defines parameters of an authentication method by creating one and then associates this method to an application by editing the application’s authentication method parameter.
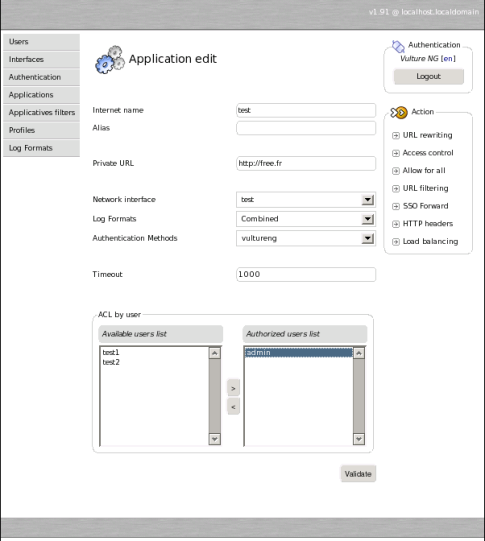
After associating an authentication method to an application you will be able to select an even more restricted pool of authenticated users using ACL. Thoses ACL are specific to an application.
SQL
Below is an example of informations needed by Vulture to do its query for authentication using SQL. Vulture support three encrytion algoritms for password comparaison besides plain text : SHA1, MD5 and Crypt.
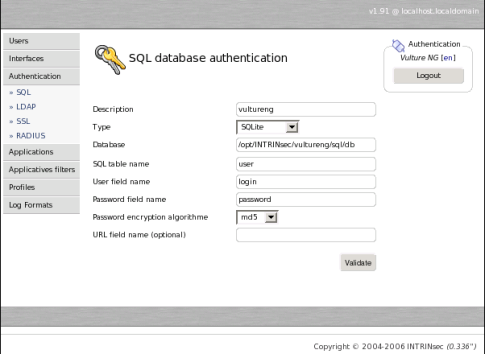
Actually, you already have an SQL authentication method configured by default which is called « vultureng ». This is the own SQL user database of the administration interface. To enable it on an application just edit the « authentication method » of this application.
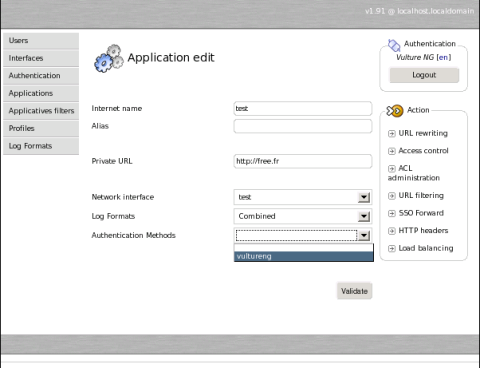
No need to restart the interface. It’s taken into account on the fly ;-).
Vulture in action
So, now, go on http://test or whatever you set the application name to and you will see this authentication form and should be able to connect using your admin account.

You can now add more users using the Users menu of the administration interface and experiment ACL by clicking on « ACL administration » in the application edition action menu.
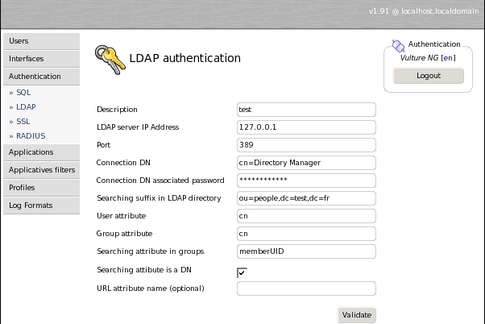
LDAP
Nothing particular here excepted for « Searching attribute is a DN ». This parameter is only needed if you plan to do ACLs regarding groups. Indeed, when looking for a member into groups, Vulture has to know either to use the whole DN of the user or just the CN. If you use an Active Directory and plan to configure ACLs by group check that. For a common configuration of a Fedora Directory Server, user, group and « searching attibute in group » would be respectively uid, cn and uniquemember. For a common configuration of an Active Directory server, user, group and « searching attibute in group » would be respectively samacountname, samaccountname and member. Otherwise, for a common OpenLDAP configuration it would be something like shown below :
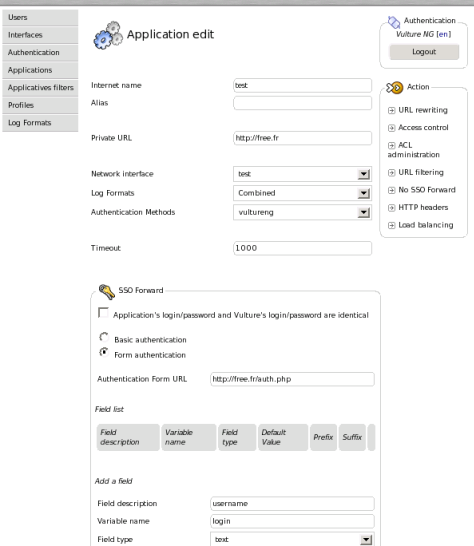
SSO Forward
Redirections
1. ^/secure => /index.php?do=secure [R]
2. ^/redirect=(.*) => http://$1 [R]
3. ^/admin => /administration [P]
4. ^/admin => [403]
5. .* => http://www.exemple.fr/enroll.php [NOCERT,R]
6. ^/admin => /enroll.php [NOCERT,P]
-
- [R] means that the redirection will be sent to the user (external) from http://www.exemple.fr/secure to http://www.exemple.com/index.php?do=secure
-
- Here is an example of perl regex : http://www.exemple.com/redirect=http://www.intrinsec.com will be redirected to http://www.intrinsec.com
-
- [P] means that the redirection will be transparent to the user and done internally by vulture itself. http://www.exemple.com/admin/index.php will be internally redirected to http://www.exemple.com/administration/index.php
-
- If there is « admin » in the URL, Vulture will return code 403 (forbidden).
-
- If the user doesn’t have a certificat it will be externally redirected.
-
- Same as in 5 but internally.
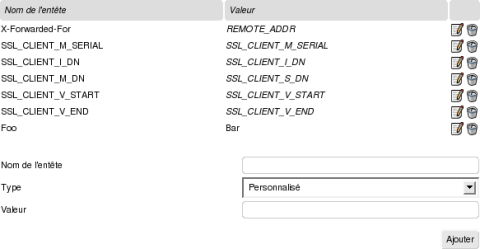
Headers rewriting